[ad_1]
Final October Robin Linus from Zerosync dropped a little bit of a bomb within the type of BitVM. One of many longest operating criticisms of Bitcoin is that it’s not doable to make arbitrary applications to manage how cash is spent or locked. Bitcoin solely has a really restricted quantity of programmability in its scripting language, and the primitives obtainable are extraordinarily constrained. You may test a signature, you may add a timelock to one thing, you may manipulate information in a couple of easy methods, however that’s it.
You may program a Bitcoin UTXO to require a signature test, a timelock verification, and so on. However you can not program it to unlock primarily based on any arbitrary situations. Robin’s perception with BitVM was that one single primitive within the subject of computing may be enforced in Bitcoin script: a NAND gate, one of many primary primitives of computing on the bodily/electrical stage. Each computation that’s doable could be constructed out of NAND gates.
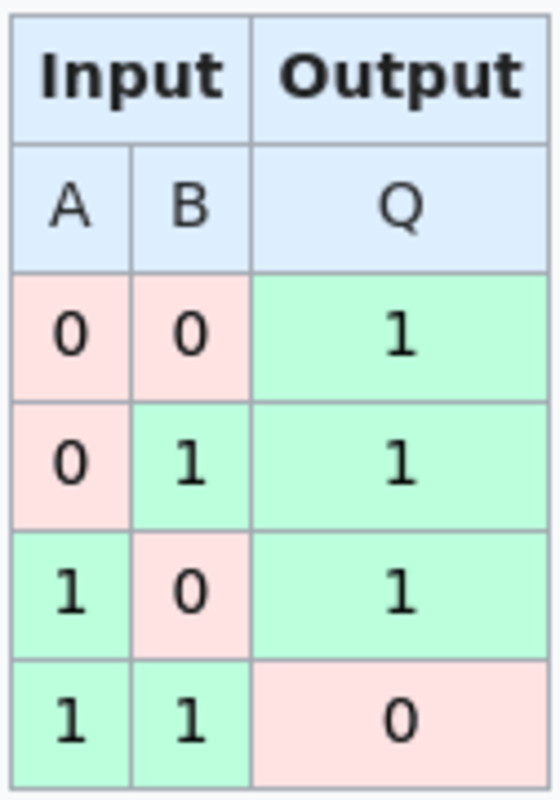
Script can really confirm a NAND gate because of a neat trick utilizing OP_BOOLAND and OP_NOT. OP_BOOLAND is an AND operation, the other of NAND. OP_NOT takes a binary 1 or 0 worth and inverts it. This collectively permits you to really implement a single NAND operation in script immediately. Together with hashlocks, a NAND gate script could be made the place every enter and output subject has two doable hashlocks to “unlock” that spending path, every one pushing a 1 or 0 to the stack to carry out the NAND operation. Every script additionally has a path the place when you can reveal each preimages to a single bit worth, you may instantly declare the funds. That is so that after somebody decides what to enter to the NAND gate, they can’t change their thoughts with out shedding cash.
A large quantity of NAND gate scripts can all be compacted right into a taproot tree, and as soon as somebody commits to the bit values off-chain to enter to that computation, the opposite celebration can problem them on any particular person step within the computation to show it’s being executed accurately on chain. Every “problem” permits the challenged celebration to show that the person gate was computed accurately, in any other case the opposite celebration can declare the funds after a timelock. Going backwards and forwards like this if a computation is contested, it’s assured that the dishonest celebration will ultimately be caught and lose funds.
The restrictions
The primary limitation of BitVM is that solely the individuals concerned in making a BitVM contract can take part, and the roles are very restricted. There’s the prover, the particular person asserting how the computation occurred off-chain, and the verifier, the one that can problem the computation and pressure it to be confirmed on-chain if the prover doesn’t full the computation off-chain or tries to lie in regards to the outcomes.
One of many causes for designing BitVM was to ascertain two method pegs to sidechains or different methods. The scheme presents a really highly effective primitive in that use case, the flexibility to truly implement funds be given to 1 celebration or the opposite primarily based on the correctness of an arbitrary computation, i.e. a validity test on whether or not a pegout is legitimate in keeping with a sidechains guidelines. The issue is, solely the individuals who maintain keys to that BitVM UTXO can really go “Hey, you’re dishonest!” when somebody is, and have interaction within the problem protocol. This finally makes the system nonetheless trusted.
One other limitation is that the problem response protocol could be very lengthy. If somebody realizes the result of the computation goes to end in them shedding cash they usually cease responding, the verifier has to basically guess the place the person NAND gate is within the computation that the prover must lie at and reveal each preimages to a bit that might give the verifier the funds. Till that particular gate is challenged on-chain, the prover can nonetheless reply accurately to a problem and drag it out. This may be very time consuming and inefficient.
Some enhancements to this design have been made for the reason that authentic proposal to permit for a number of verifiers to exist within the system with the prover, to create a 1-of-n belief mannequin the place solely a single verifier is required to problem a dishonest prover. Nevertheless, this requires the instantiation of a number of BitVM cases in parallel to perform, and subsequently will increase the inefficiencies with the unique two celebration design.
BitVM 2
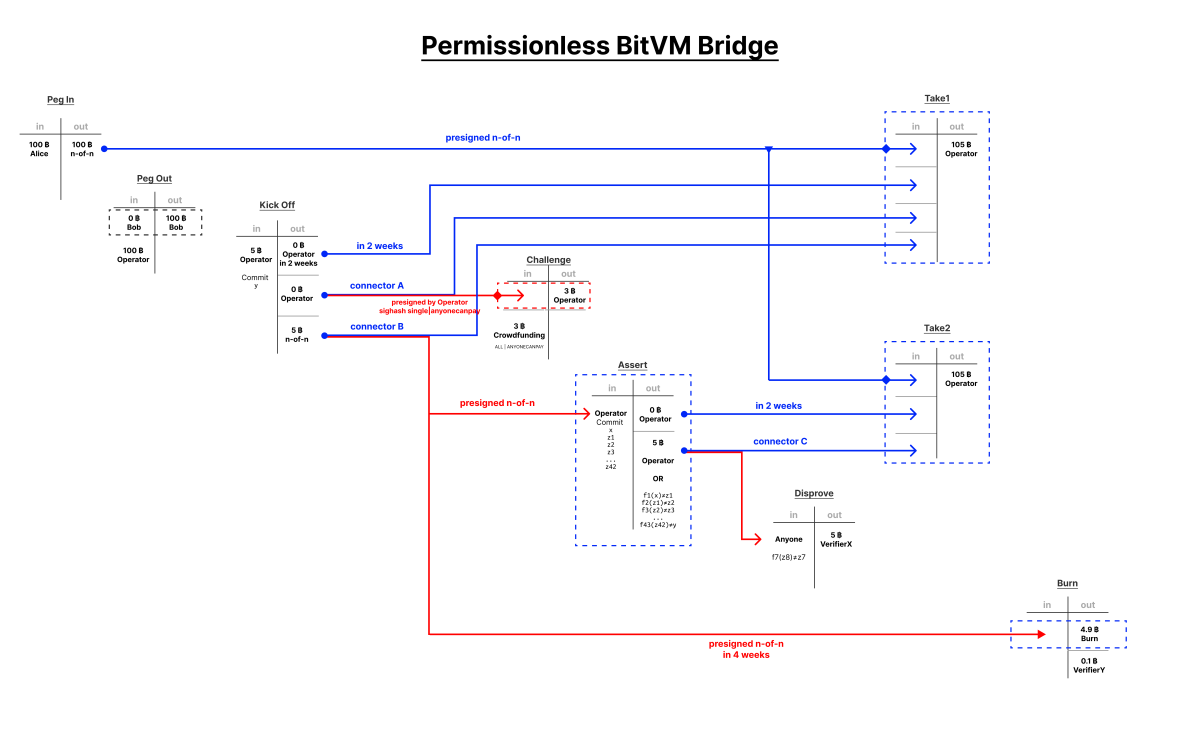
Robin not too long ago proposed a design scheme for BitVM 2. This scheme seeks to make a couple of commerce offs compared to the unique design for the advantage of mitigating its two main shortcomings. BitVM 2 shortens the problem/response protocol size from an indeterminate sequence of transactions that may very well be upwards of dozens within the worst case situation, to 2 rounds within the problem/response. Along with this, with using connector outputs it permits anybody to behave as a verifier. It doesn’t require somebody to be a member concerned in establishing the BitVM to problem a dishonest prover.
The basic shift right here is shifting away from immediately utilizing script NAND gates to implement the uncooked computational hint immediately, and shifting to utilizing them to implement a common SNARK zero information proof verifier (one of many core primitives Robin meant from the begin to implement utilizing BitVM). As a substitute of placing the uncooked enter into the uncooked computational hint, and operating it gate by gate in their very own tapleaf scripts, the enter of the BitVM 2 occasion would merely be a zero information proof enter together with an asserted output of the computation.
Along with abstracting away the computation implementation with a ZKP, the tapleaf scripts are being massively expanded from a single NAND gate per leaf to a complete sub-function of the ZKP verifier. As a substitute of the problem response protocol being primarily based across the verifier guessing at which NAND gate the prover tried to cheat at, selectively difficult at a single gate, the verifier can show a complete sub-function’s output is invalid in keeping with the enter.
Similar to BitVM 1, the contract is pre-negotiated utilizing pre-signed transactions and branching scripts. Funds pegged into the BitVM are despatched to an n-of-n multisig which indicators two doable execution transactions, one wherein no problem happens, and one wherein a problem happens. To begin the method of executing the contract, the prover initiates a kick off transaction. This kick off transaction commits to the output worth ‘y’ they declare the computation produces, and contains three outputs: a timelocked output that’s included within the no problem execution transaction, a connector output A, and a connector output B, each of which are also spent within the no problem transaction.
Right here is the place the design permits for anybody to take part as a verifier. Connector output A has a second pre-signed transaction that may spend it, the problem transaction. It is a pre-signed transaction that pays the prover a bond in bitcoin, however the connector output A will not be sufficient to fund it. Actually anybody can add their very own inputs to fund the transaction and spend connector output A, which invalidates the no problem withdrawal transaction for the prover (one of many inputs it wants no problem exists).
This forces the problem path. Connector output B can be spendable utilizing a pre-signed transaction, the assert transaction, to the output of each sub-function in the whole BitVM 2 contract. This requires a big transaction with loads of information, however keep in mind, the final word output ‘y’ the prover is claiming the computation produced was already dedicated to within the kick off transaction. This creates two outputs. One is a timelocked output, the opposite is a connector output C. Each of those outputs, along with the unique pegged in funds, are all spent within the second profitable withdrawal transaction for the prover after the timelock.
Connector output C can be spendable by anybody who can show that any sub-function output within the BitVM 2 contract produces an invalid output. This requires a really giant transaction, as a result of the script essential to show a complete part of the BitVM computation is wrong is very large, however on this single transaction a verifier can declare the cash within the connector output with a sound proof. This invalidates the second withdrawal transaction for the prover and successfully burns the cash. The one approach to get better them at this level is that if the prover and all of the verifiers within the authentic n-of-n funding multisig all cooperate to get better them. Connector output B within the kick off transaction may also be spent after a for much longer timeout than no problem withdrawal to invalidate each the no problem and the assert transaction, burning the pegged cash.
This reduces what may very well be a ridiculous chain of transactions within the authentic BitVM proposal to implement the proper contract final result, to at most 4 transactions (though admittedly very large ones), whereas within the course of making the set of verifiers for the BitVM 2 occasion actually anybody with bitcoin who will fund the problem transaction.
BitVM 2 may wind up being a big breakthrough regarding the wave of rollups and different layer 2s aiming to make use of BitVM as a two method peg. The operator of a rollup (the prover within the BitVM) can use their very own funds to cowl withdrawals of customers who’ve pegged into the system, and periodically withdraw these funds from the BitVM to compensate themselves. Any consumer or celebration would then be capable to penalize them by burning their funds if they may produce proof the operator was not processing all withdrawals accurately.
It is very important observe that finally the safety of a BitVM 2 occasion is backstopped by the n-of-n keyholder, though individuals not collaborating in it could actually nonetheless problem the prover as a verifier. However as a result of the prover has an environment friendly exit within the case of no challengers, and anybody can fund the problem transaction to behave as a verifier, the n-of-n funding multisig may observe a setup and key deletion ceremony just like the Zcash launch to enhance its safety.
BitVM 2 will in all probability wind up being a big breakthrough when it comes to bettering the flexibleness and belief mannequin of two method pegs that make use of BitVM. As soon as once more, Robin has confirmed himself an actual wizard.
[ad_2]



